/home/voxx-vindictae/blog/002_op-monoxide.html
guest:~/blog]$ htmlview 002_op-monoxide.html
I. Introduction
>The Canary Mission was established in 2014, and since then has gained notoriety for its extreme tactics. The site purports to expose antisemetism by holding people accountable for their online posts and communications. But even that claim is dubious, as their page states that the organization
>"...documents individuals and organizations that promote hatred of the USA, Israel and Jews on North American college campuses and beyond." (Source: Canary Mission About Page)>
What this looks like in practice is more akin to doxxing activists that express any support for Palestinian Liberation or express criticism of Israel's actions concerning said liberation. Canary Mission's intimidation has been criticized as a chilling effect on free speech; employers, US law enforcement, and even the Israeli Government have used the lists put together by Canary Mission to single out pro-Palestinian Protesters.
>So naturally, I decided to investigate this further. Since my last post here, I'd picked up a couple of additional skills that prepared me well for an investigation into the workings of the Canary Mission foundation.
>What I was not prepared for, however, is what I would find.
II. Scratching The Surface.
>As with any research project, I started by checking what others already knew. The members of the Canary Mission have remained anonymous (understandably so; I don't think anyone doing what they were would like the taste of their own medicine), apart from two notable figures.
>In their investigation into Israel's influence in the United States, Al-Jazeera identified Adam Milstein as the main source of funding for the Canary Mission. But I wasn't interested in the funding so much as I was in the operations. So I kept digging.
>After a while, I stumbled upon an email screenshot recovered by the GrayZone Project. The screenshot showed the Canary Mission domain as being registered through GoDaddy by one Howard David Sterling.

III. Delving Deeper
>Now that I had a lead, I did some reconnaissance to see if I could verify the GrayZone Source.
>First, I chekced the historical DNS records (type NS) of the site using Security Trails.
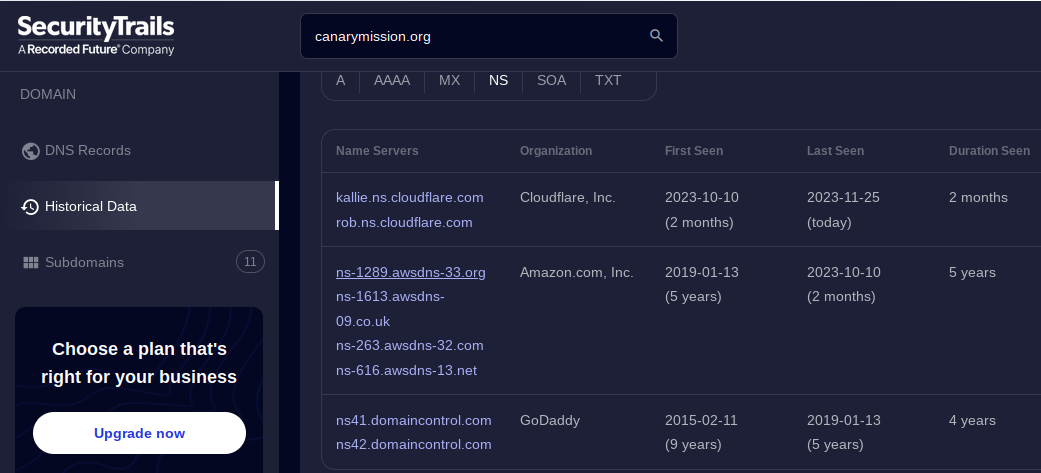 >
> You can do the search yourself, but you need an account to see the interesting stuff. Fortunately, One of the resources linked on this site helps with that. Using my totally legitimate and not at all shared account allowed me to see that the domain was indeed first registered through GoDaddy, and was indexed less than a day later. This corroborated the source from GrayZone, but was far from the most interesting aspect of the results.
>The first thing I noticed was that the IPv4 records (type A) indicated that from 2020 to 2023 the hostname redirected to a hosting provider in France, SCALEWAY S.A.S. This would turn out to be significant later in my investigation.
>The second thing I noticed was that when the domain was first registered, the domain name pointed to an IP owned by O.M.C. COMPUTERS & COMMUNICATIONS LTD., an ISP based in Israel!
>This changed my entire understanding of what the Canary Mission actually was: an attempt by the Israeli regime to suppress Palestinian Solidarity. Howard Sterling was known to invest in Israeli companies, stating in an IsraelCast interview:
>"People will protect their pocket books. And if they have shares in Israeli companies, they are going to want to protect their pocket books by protecting Israel.” (Transcribed from GrayZone Source).>
It only makes sense for him to support this as well, especially given his experience with tech companies. He would know how a website worked, how a domain was resolved. and he had the financial motivation too.
>I could've stopped here. After all, I'd proven that the GrayZone source was reliable, despite what Sterling's lawyers claimed. And by hosting in Israel, the server would be subject to any searches performed by the Israeli Government.
>But I didn't stop there. I wanted to know more. So I kept digging.
IV. Constructing A Timeline.
>I used a Metasploit Auxiliary module to enumerate all the subdomains of the Canary Mission Website by pulling them from the pages cached on the Internet Archive. This told me a number of things about the site itself:
>- The site was built using Wordpress at one point.
- The site currently uses meteor.js as a way to get database content for the web browser.
- meteor.js uses MongoDB as its database.
- The domain
beta.canarymission.orgappears in the list of subdomains.
A whois search for the beta domain revealed that the beta domain points to the original host for Canary Mission, as proven by the timestamps in the whois data matching those in the email screenshot. What's more is that the domain was updated in October of 2023.
>My going theory is that when the main website was moved to use Cloudflare servers, the beta domain was left on the French host, as it wasn't accessible through the web anyways.
IV. Pulling Back the Curtain
>I checked another DNS History service, dnshistory.org, for any records my other dources might have missed. I found an IP that was in this French network, which resolved to canary.fixweb.net. A search for the domain fixweb.net revealed another domain: ief.fixweb.net.
I don't remember why this domain caught my attention, but I'm glad it did. Using nmap on this host revealed that it was hosting quite a few services: a PureFTP server, OpenSSH, the usual HTTP/HTTPS ports and... a database.
>A search for "IEF" pointed me to a discontinued tool called Internet Evidence Finder, developed by a Canadian Digital Forensics company called Magnet Forensics. The tool was designed to aggregate and link internet data for use in law-enforcement investigations, a purpose that is problematic even outside of the context of my investigation. Regardless, I hypothesize that the CanaryMission is possibly using IEF to gather its data.
>EOF
Part 2 can be found at /home/voxx-vindictae/blog/003_op-monoxide.html